DHS Finds Most Critical Infrastructure Attacks Involve APTs
More than half of the 245 security incidents reported last year by critical infrastructure entities involved sophisticated actors, known as advanced persistent threats, according to new data from the Department of Homeland Security.
The incidents involved exploitation of zero-day vulnerabilities in control system devices and software; exploitation of web application vulnerabilities; targeted spear-phishing campaigns; and network scanning and probing. Sophisticated attackers weren’t the only ones compromising critical systems. Organizations are also battling against hacktivists, insider threats and criminals. Roughly 55 percent of the reported incidents involved APTs. But because of a lack of data necessary to make attributions, organizations often could not identify their attacker.
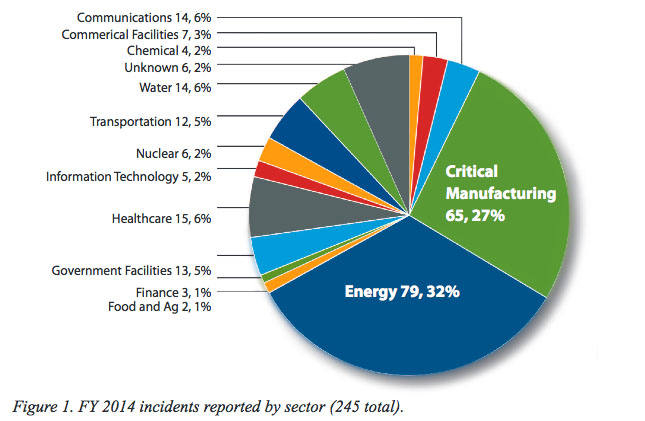
About 30 percent of the 245 incidents reported to the DHS’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) came from the energy sector. The critical manufacturing sector, which includes manufacturing of vehicles and aviation and aerospace product and parts, accounted for 27 percent of the reported incidents. Government facilities reported 13 incidents last year, or 5 percent of the total number.
ICS-CERT said these incidents reported by asset owners or through relationships with trusted third parties represent only some of the incidents involving critical systems. “Many more incidents occur in critical infrastructure that go unreported,” ICS-CERT noted. Organizations reported 11 fewer incidents in 2013 compared with last year.
Organizations are encouraged to report malicious activity, even if they don’t need assistance, because ICS-CERT uses that data to provide potential victims with situational awareness as well as information about an attacker’s techniques and tactics. “All sensitive or proprietary information reported to ICS-CERT is protected from disclosure under the Protected Critical Infrastructure Information (PCII) program,” according to ICS-CERT.
Organizations Lack Monitoring Capabilities
Although organizations are able to confirm they have been compromised, in most cases they don’t know what method an attacker used. Their “forensic evidence did not point to a method used for intrusion because of a lack of detection and monitoring capabilities within the compromised network,” ICS-CERT explained.
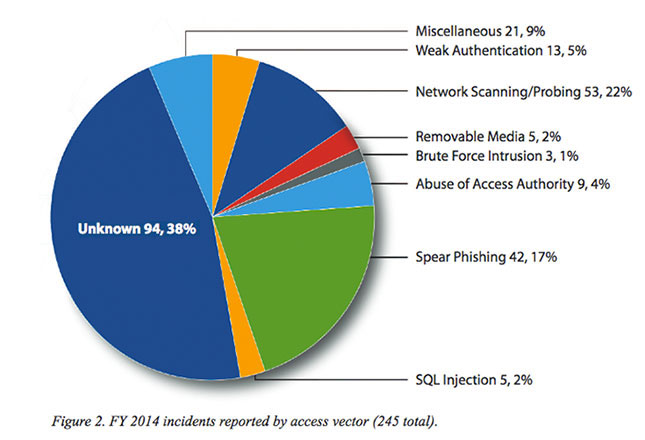
For 38 percent of the reported incidents, organizations could not identify how their environments were compromised. Organizations that could identify their attackers’ methods said spear-phishing and network scanning and probing were the most common ways for intruders to gain access to systems.